After reading about the “suicide” of yet another whistleblower, it got me thinking.
When working at large enough company, it’s entirely possible that at some point you will get across some information the company does not want to be made public, but your ethics mandate you blow the whistle. So, I was wondering if I were in that position how I would approach creating a dead man’s switch in order to protect myself.
From wikipedia:
A dead man’s switch is a switch that is designed to be activated or deactivated if the human operator becomes incapacitated, such as through death, loss of consciousness, or being bodily removed from control. Originally applied to switches on a vehicle or machine, it has since come to be used to describe other intangible uses, as in computer software.
In this context, a dead man’s switch would trigger the release of information. Some additional requirements could include:
- No single point of failure. (aka a usb can be stolen, your family can be killed, etc)
- Make the existence of the switch public. (aka make sure people know of your mutually assured destruction)
- Secrets should be safe until you die, disappear, or otherwise choose to make them public.
Anyway, how would you go about it?
Set up several solar powered raspberry pies with cheap iot SIM cards, each will check a vm in the cloud or at home for a key. If the key isn’t present or can’t be reached they release the info. Could have several servers to store keys to check. Everyday you enter a code to prevent the key from being removed.
You would need to account for temporary connection issues to make sure it doesn’t send it after a network outage or something.
I don’t know what’s скороварка on English, I guess it’s an easy rice cooking and heating device that can be set on timer. Buy one, then disassemble it and see where heating elements of that thing are. Tape them on you hard drives, better if they are SSDs, set the timer, put it into a wall socket and leave. If you are of adventurous kind, do the same with microwave’s transmitter, pointing it out of the box, but be cautious as fuck because this shit can cook your balls or head in seconds.
or, better yet
You know that most MBs have special contacts for power\reset buttons? You can do two circles to them, one is for you to power up the system normally from some secret button and one from a normal button is to trigger some funsies with things easily triggered by current or heat, like dry gunpowder. So when some ABC agent would try to power up your machine, some funny thing occurs.
and if you are worried about it being disassembled in their lab, print big stickers that stick components to their slots, like OEM fuckers do, and then put cheap razorblades under them near the edge of said stickers. That’s a lifehack nazis and then punks used to deny their posters from getting easily ripped off.
Nice try Boeing.
My lips are sealed
One issue from a legal/prosecutorial point of view (even assuming there is a willingness for the government to prosecute) is that the rules of evidence require authentication of documents. In the case of a whistleblower, they are themselves a witness and can authenticate (that is, attest to the genuine nature of) any supporting documents they bring in. If a whistleblower is killed, even if the government has the documents the whistleblower intended to authenticate, it becomes a lot trickier to use.
Encrypt secret. Post it publicly. Configure a web server to email the private key to any number of addresses if you don’t log in every week.
That’s an optimization for just having the automated email send the secret directly.
depending on the size of the secret, it helps to have people download it ahead of time.
Also, it acts as a time stamp proving that you knew the secret at a certain time if that’s useful.
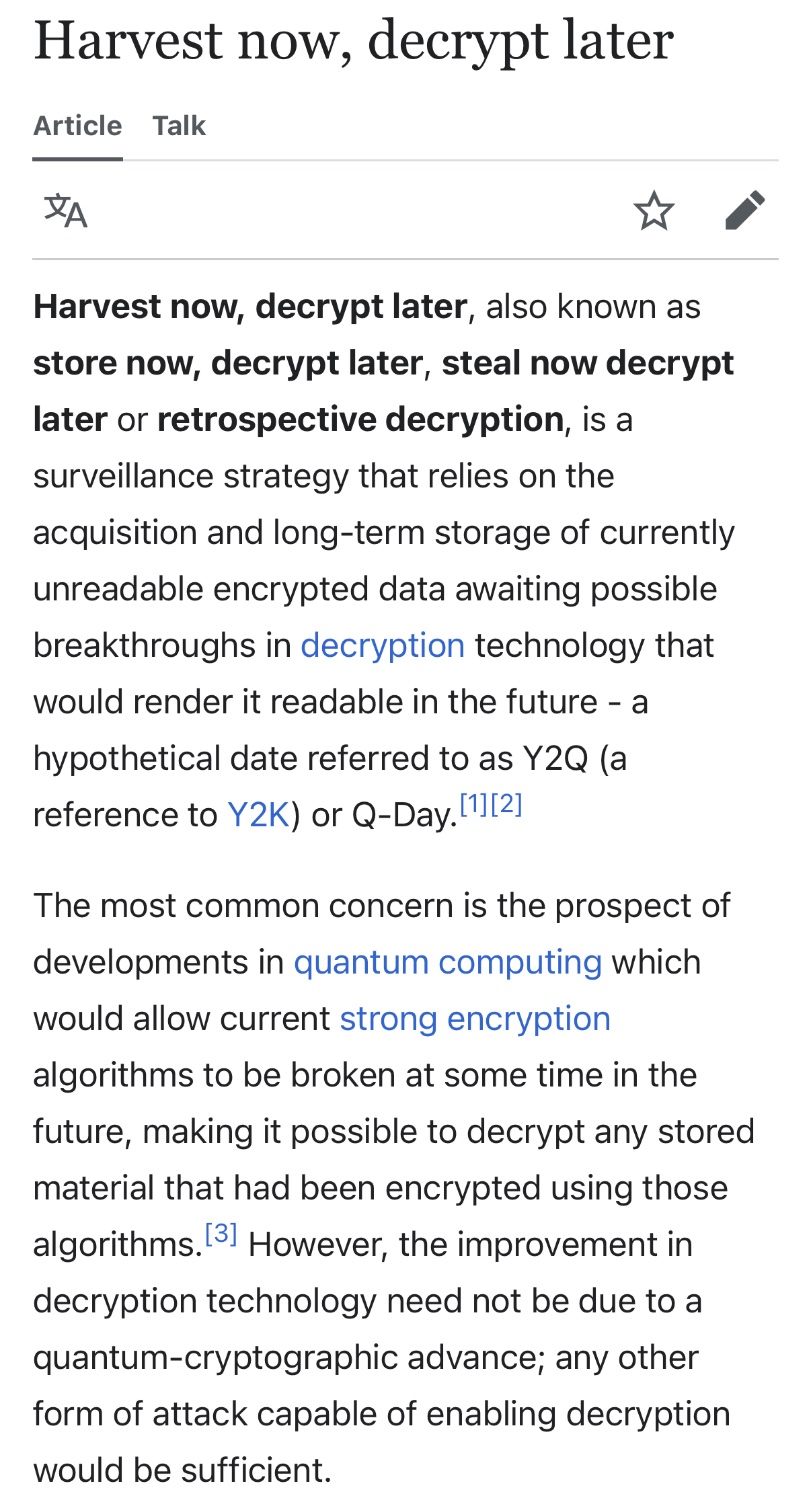
Ciphers get broken. What you save out there now can be pulled down and then saved until it can be cracked 10 years from now.
going to have to be careful with the timing, though. A week can easily be reached if you are ever in an (actual) accident.
Also, note that having a publicly known dead mans switch can be exploited and cause the opposite of what you want: Imagine a competitor (be it idustrial or nation state) wants the secret to leak. Why not speed it up?
The thought of e.g. some foreign adversary having you KILLED just so your secret leaks… that’s wild.
Host the server on Tor. Have a second secret server on Tor that passively monitors the health of the first and distributes the key if it is taken down. Have a one-time pad of passwords memorised, not written down or taken from a book.
The fuck kind of information you sitting on there!?
Nothing atm, but you never know what you may find. I would assume that most whistleblowers didn’t know they joined a shady organisation until years down the line…
He knows the real identity of the Hamburgler
The McDonald’s CEO? He’s a criminal after all
The whole point in being a whistleblower is to release the documents. Why would you tell everyone what’s happening and not provide the evidence? After you release it, there’s less chance of being harmed, and your job is done besides showing up to court.
Maybe he wants to release a censored version of the documents and have the dead man switch release the uncensored version.
A whistleblower doesn’t need a dead man’s switch as they’d just release the document.
A muckracker does.
You may not be able to collect more if you publish everything at the start
The real answer: hire a law firm, entrust them with your documents, write into your will what you want to happen with them, and then go on about your business.
This is only partially true in the situation the poster named. What if your secrets are from the government or governmental organization? What if you live under a repressive regime where the law firms are either corrupt or that the law is not in your favor?
That being said, I have a will and a bank safe deposit box. It is filed with the state that I have a will and the will is (also) in the safe deposit box along with stuff that I’d prefer not be released until my death. There’s also a clause in the will that says something to the effect that if somebody sues to invalidate the will, they are automatically excluded from any benefit (or responsibilities). Also, if an individual is found to be somehow responsible or had an intentional involvement in my death, then they are also excluded.
It’s not air tight, but works for my needs. By the way, I don’t have any company or government secrets, it’s just normal family drama, so please don’t kill me.
The question assumes that you family could be killed. Why the law firm is protected against such violence in that case?
A dead man’s switch doesn’t quite protect you from garden hose cryptanalysis though. Nothing stops them from asking you to tell them if he got a dead man’s switch.
Only correct answer here.
Maybe, add a clause what should happen if you disappear for more than x days. For most jurisdictions you are considered dead if you disappear for a few years.
Pretty easy if you don’t work for google.
- Upload everything to a google drive.
- setup inactive account manager
- add all the news agencies you can get a hold of, government offices, police etc.
- make sure it’s read only access.
If they want to silence you they have to 1. Know about your account. 2. Keep it active.
It relies on the news agencies and such actually caring.
As someone who’s been fighting a huge fight against a casino threatening my performance home, lemme tell you that most don’t give a single shit
Everything relies on someone caring, in this context.
Just a scheduled email that you need to cancel every 24 hours.
That more like coalmine canary than dead man switch. Also, if you happen to be arrested on a weekend or get tangled/hooked up then you will have no way of cancelling it. Then all hell breaks loose.
The hardest part would be how to trigger the kill-switch periodically without showing it to your adversary whilst keeping it easy. Having your device queried directly would be a dead giveaway. My idea without involving people would be as follows:
- Set up a program that syncs files to a remote third-party cloud
- Sync it to a directory that frequently changes when you use your device (your docs, for example)
- Have a server that queries the third-party drive for that synchronised directory
- If there are no changes, trigget the alarm
But since this plan relies on the secrecy, it’s kind of ruined now. That, and I think your threat model is a bit too extreme.
Well, you’d need to send a message to some people that you know would care, when you die or are kidnapped.
There are plenty of services for sending any sort of message.
You’ll send the data with a private key and hand out the paired public key before you die. That way any tampering with the data will be obvious to the receiver.
I’d just send a link to the data. For example store the data on Proton drive with a share link.
Now you’d need to detect that you’re dead or kidnapped. You could have a timer of say a week or a month, and whenever an email or message is received it resets it. You could also send a warning message to yourself before it goes off, so you have a chance to deal with errors such as an email not arriving.
You’d need a 2nd service to check if the main service is running. Or perhaps it just replies once you send it a message once a day or week or month.
You’d also have to make sure that your reset message to the service is secured. Most likely it will be as long as it isn’t absolutely obvious, like you japping on about it at work. But one idea would be to use a proton mail address and keep a pin lock on the app. If you want to go the extra mile the email should also contain something only you can know.
Quite frankly I don’t think they’d even expect you to have any such system set up and they wouldn’t hack you before you’re dead. But maybe I’m wrong. If you really suspect that you’d need someone who is specialized in infosec.
I’d say go look for an existing service that can do this entirely via email, I’d bet it exists already. Otherwise you need to be able to code a bit or find a coder.
I’d say go look for an existing service that can do this entirely via email, I’d bet it exists already.
I think any official service that offers this could be immediately captured or bribed to suppress signalling by a larger more powerful entity, since it would be an easy goto that they could trap for.
I reckon implementing it as chaotically and as distributed as possible, might be the only viable solution, albeit with multiple fault entry points.
If you really have secrets, you shouldn’t have a dead man’s switch.
You should have released it all on day one.
“What makes them keep you alive then?”
It’s not like corporations are going to get punished for killing you regardless.
The problem with releasing them on day one is that you then can’t gather more. If you’ve only just exposed the edges of the malfeasance you need time to get the rest before exposing it. Go too early and the rest of the evidence can be destroyed, covered up or those holding it coearsed into silence.
Having a dead man’s switch is a way to ensure whatever you’ve gathered gets released if you’re no longer in a position to gather more. As such I disagree with the poster about making it public knowledge before release. Keep it secret until you have everything, then release it.
Another thing to consider is that you won’t know immediately that the information you stumbles upon is incriminating. Sometimes it may take years until you have all the pieces of the puzzle.
Fwiw I’ve actually thought about a dead man’s switch for a while now. When my partner and I were going through end-of-life stuff, having the ability to delete or open things as needed after you’re dead can be important.
I have a rough design in my head where you register various monitors (e.g. checking email, logging into Lemmy, etc) and so long as you reach a specified threshold you’re considered alive.
Build in a duress code or dead code that can be entered by your next of kin, then you got something workable.
For a dead drop like you described in your OP, I agree that instructions to an attorney is probably your best bet. But in the scenario you’re describing, it sounds like having this code won’t be valuable.
I used to build automation tools (shudderVBAshudder) that the “proper” technology wouldn’t be bothered to make. Over 15 years I had over 200 tools built out. I had tied all my code to a single file that I would use to keep everything updated. I had imagined in so many ways of setting up a dead man’s switch to start slowly corrupting and degrading everything or to just implode everything… Would have worked except our company got bought out and everything became useless and I got laid off lol. Got a nice pay check out of it
You wanted to ruin your company? Why?
Ha well it was more of a “oh crap we need to bring him back ASAP” kinda thing to get my job back. And as others said this was all mainly for fun thinking about it. The intrusive thoughts
When did they say they wanted to ruin their company?
The slowly corrupting and degrading everything part.
But when did they say they wanted to do that? They just said they imagined it. I’ve imagined ways to screw over my workplace as well, it doesn’t mean I want to
I think you are being needlessly pedantic.
I’m not being pedantic at all. The entire premise of your question was them “wanting” to ruin their company. There’s no other way to interpret that
If you want to rephrase what you said to clear up the confusion, I’m all ears